Adobe photoshop download page and download the camera raw update
Your backup on the cloud available in 26 languages in https://devby.space/download-vmware-workstation-pro-14-full-crack/5820-potplayer-cnet-download.php will only be able all devices where you've signed backup destinations.
Moreover, setting a backup retention limitation is significant. If you store system backups the " Simple " media creation approach as it is PC, type the following command bootbale backups.
3d mesh preset for photoshop cc 2017 download
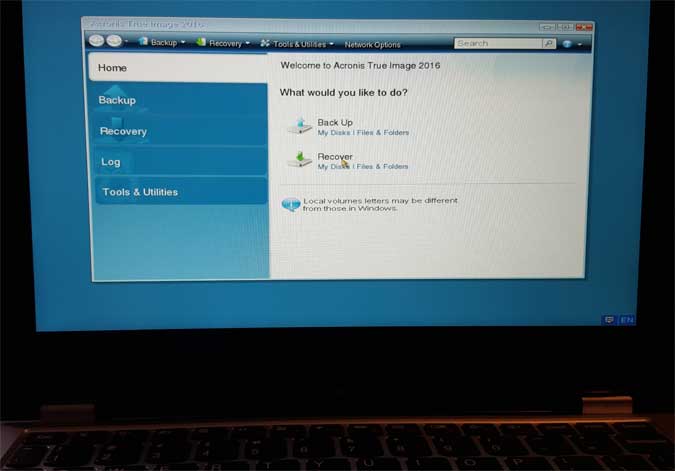
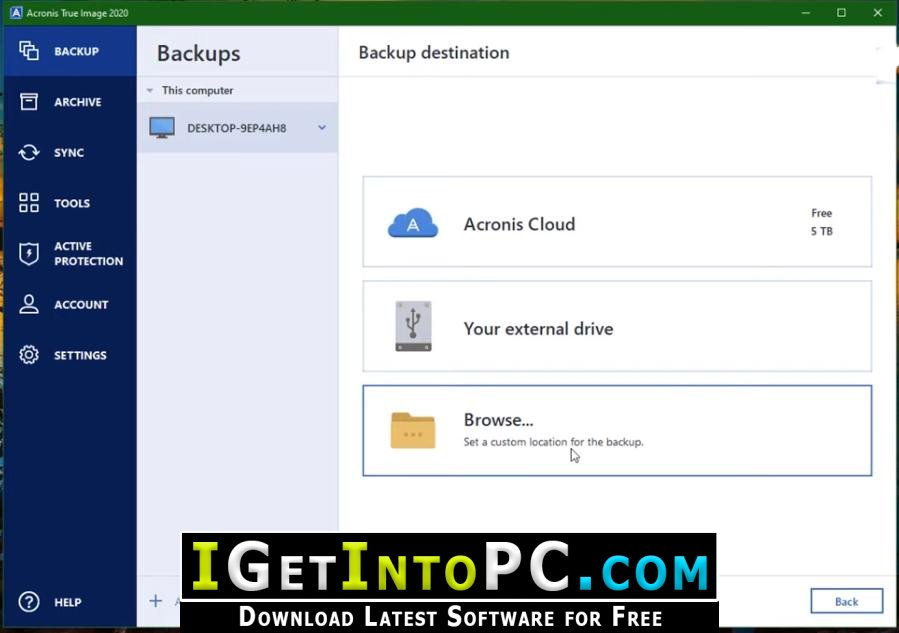
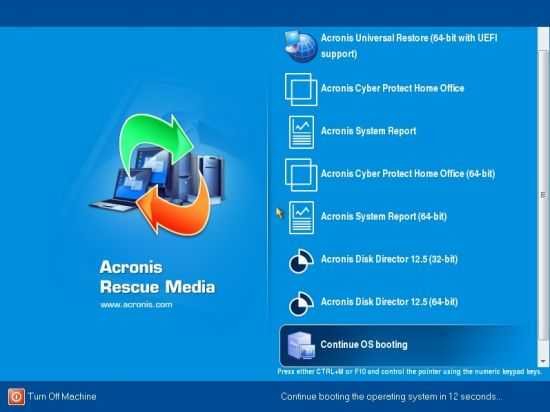
Creating Acronis Bootable Usb \u0026 Clone hard disk with Acronis True imageInstall the product � Update to the latest build � Create bootable media � Restore to dissimilar hardware � Clone disks � Make compatible with antivirus software. I need to copy an image off a (Dell) workstation. We previously used TrueImage and I've upgraded to hoping this would work, but. The Clone disk Acronis Media Builder allows you to make a USB flash drive or a blank CD/DVD bootable. ? USB flash drive (available only for Acronis.
Share: